JSON Web Token (JWT)
Are you also the one among many who think authentication and authorization are the same? It's a brand NO.
Before going into JSON web tokens, let's first understand the difference between the two terms.
Authentication & Authorization
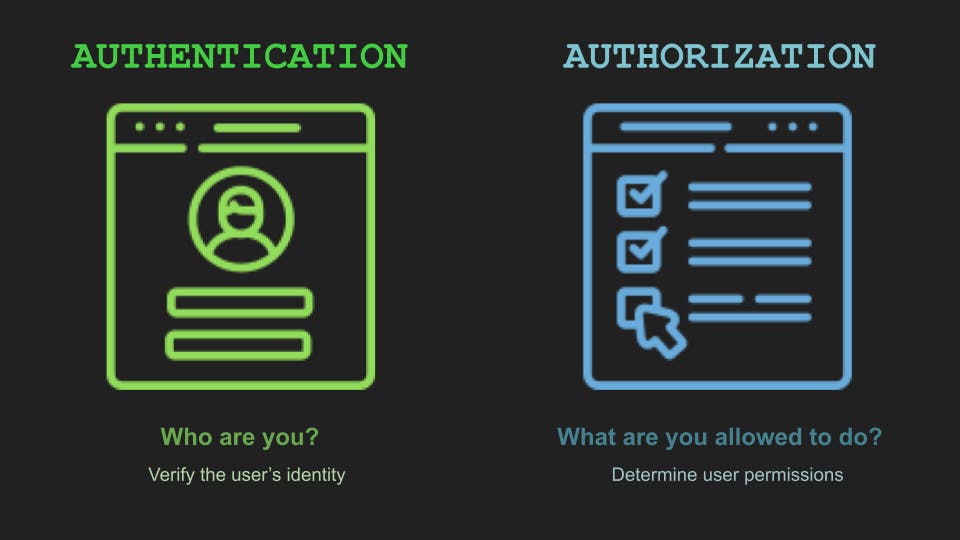
Authentication: This is when you are uniquely identified against your credentials. Your credentials may include your username, email, password, etc. This is one of those terms that we come across in our everyday lives. Be it logging in to your bank's website to check your transaction details, an e-commerce application to buy what you are in need of, or even accessing your emails.
Authorization: Authorization comes into the picture after you are successfully authenticated. You generally don't authenticate yourself just to land on some web page. You do so, to perform some actions. Comparing the same analogies from authentication, if you have logged in to your bank account, it may be to transfer your money to some other person or maybe to change your password, and similarly if have logged in to your e-commerce application, it will be to order your favorite products or to Wishlist the items you want to buy in future. These actions can only be performed when you are authorized to do so. And this authorization happens through a unique token, called the JSON web token.
Now that we have familiarized ourselves with the two terms, let's try to understand JSON web tokens in detail.
Definition: JSON web token is an open standard used to securely transmit information between parties as a JSON object. This information can be verified and trusted because it is digitally signed.
After a user is authenticated, there are two ways in which the application knows it's YOU who is performing the actions. One is through session ID and the other through JSON web token.
Whenever a user authenticates on an application, the server stores that user and assigns a unique ID (session ID) which is sent back to the browser in the form of a cookie. As long the user stays authenticated, the browser holds this session ID and passes it every time the user makes a request. The server then validates the session ID and provides the response.
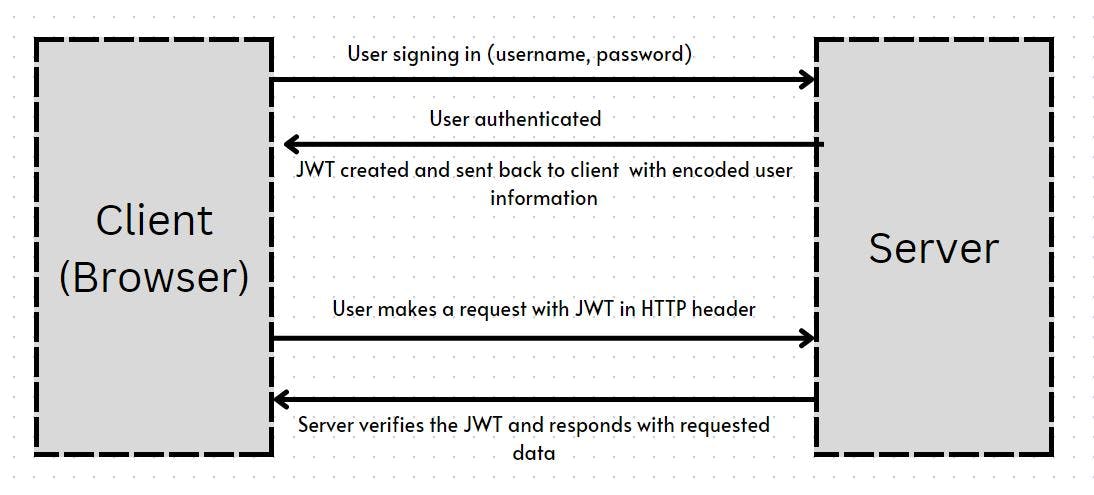
In the case of a JSON web token, when a user authenticates, the server creates a JWT, signs it with a secret key and encodes all the user information in the token, and sends it back to the client (browser). Unlike session ID where the user information is stored inside the server, in JWT, the server literally holds nothing. Everything about the user is held in the token and this is then sent to the server whenever the user makes a request. The server then checks for the token validation and provides the necessary results.
JWT authentication flow
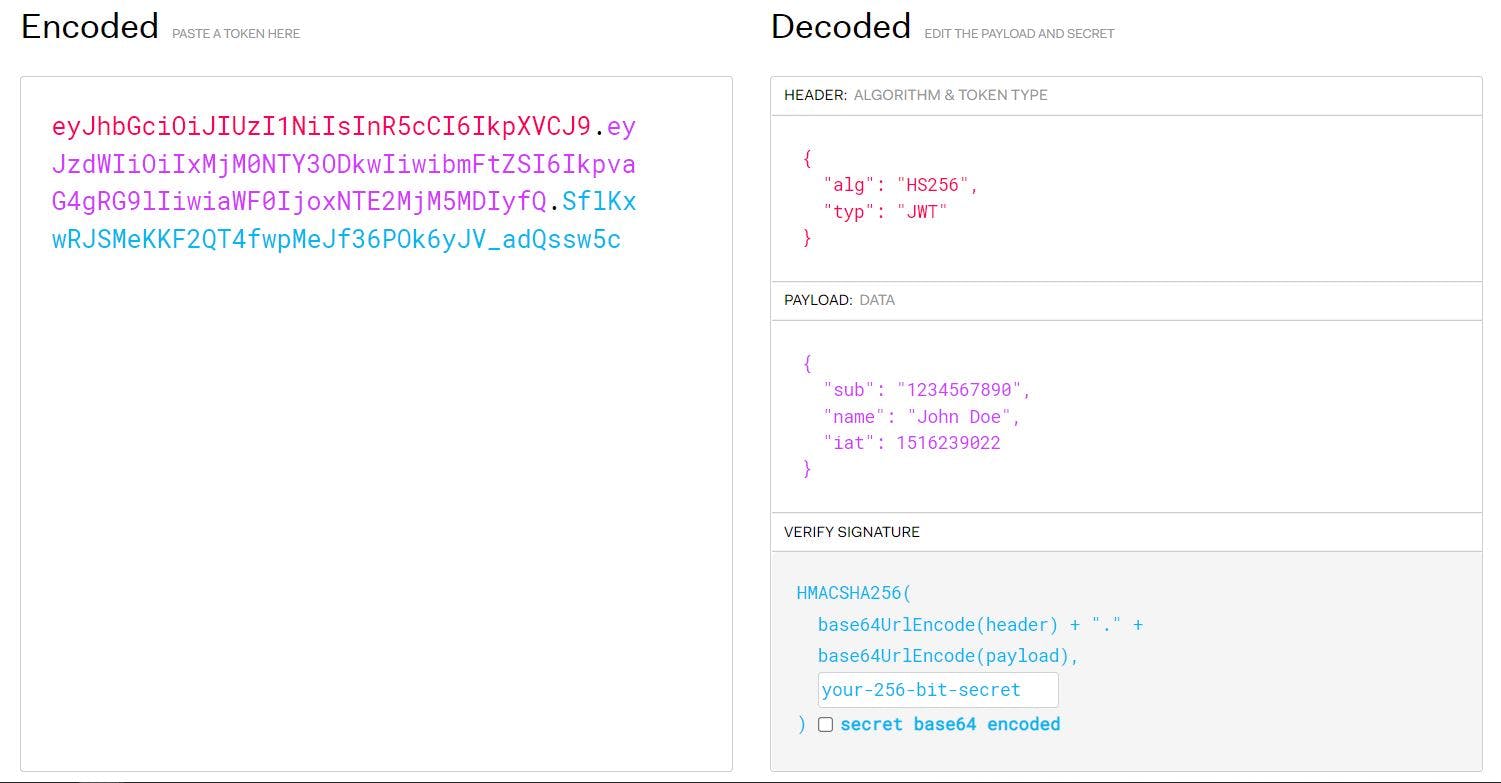
JSON web token structure
Let's now understand, how the JWT is created and signed.
A JWT essentially consists of a series of alphanumeric characters (aaaaaaaa.bbbbbbbb.cccccccc) and is divided into three parts.
Header: The header is where the signature algorithm sits. It also consists of the type of token, which in our case, is JWT. There are numerous algorithms that can be used to sign the token. Some of the popular ones are, HS256, HS384, HS512, RS256, RS512, RS384, etc.
{
"alg": "HS256",
"typ": "JWT"
}
Payload (Data): Payload contains a set of properties or claims which are not mandatory but are recommended to provide. These claims include username, unique ID, expiration time (the duration after which the token validity expires), etc.
{
"sub": "1234567890",
"name": "John Doe",
"admin": true
}
Signature: A signature is created by signing the header and the payload. This is accomplished by using the algorithm provided in the header part. A signature is used to verify the user and it checks if there was any change made to the token. If yes, it doesn't authorize the user else, it provides the requested data.
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret)
Visual representation of JWT
Advantages of using JWTs
- They provide a built-in expiry mechanism
- Server doesn't have to store the user information in its memory
- Mode of verification is highly reliable
- Highly adopted in single sign-on solutions
- Provides a wide variety of algorithms to verify the token
Conclusion
In this blog post, we understood the overall picture of what JWTs are and how they are used for authorization. Although JWTs look simple, there is a lot behind the scenes. A simple error in using the algorithm may cause a massive impact and may even lead to data theft. But if implemented correctly, JWTs can be very useful and reliable.